Company | 03/13/2019
Keeping Our Edge: the Attack Lab

In our previous article, we discussed Ledger’s bounty program with our Chief Security Officer, Charles Guillemet – an initiative to keep increasing our security. Today, we interview Charles regarding our attack lab called the Ledger Donjon, where we use cutting-edge technology to seek out any potential vulnerabilities in security-related solutions.
What is the attack lab and what is the goal of having one?
An attack lab is a high-level security research facility, operated by security researchers that enables us to perform sophisticated and in-depth tests on the security of our devices. I firmly believe that even if you design the most secure system, you will never fully know if there are any vulnerabilities until you test and evaluate it properly – nothing beats an attack-oriented mindset when it comes to assessing security.
For our security assessment, we use a wide range of attacks, including software attacks, side channel attacks and fault attacks. We discuss these in detail in both the Secure Element and Ledger Donjon articles. For the creation of our devices, we collaborate closely with the firmware and hardware teams. This collaboration continues even when the product is finalized. If we find any vulnerabilities, we evaluate the potential impacts and discuss this with the firmware and hardware teams as well and find possible mitigations and countermeasures. This assessment of our products is an ongoing, long term process to ensure our customers with the best and most secure product we can provide.
What is the attack lab’s priority regarding security in the cryptocurrency world?
The Ledger Donjon’s first and foremost priority is and will always be to find vulnerabilities in our products and help counteract these. This is, however, not our only focus. We strongly feel that all cryptocurrency related companies have a shared responsibility in guaranteeing a high level of security for the industry as this is a very serious matter. At Ledger, we work not only to keep our own security at a high level, but equally evaluate the security of products in the cryptocurrency ecosystem. Following a responsible approach, we advise them and help them to maintain a high standard as well. Any findings are disclosed responsibly, as explained in our bounty program article.
What does the attack lab workspace look like?
The Ledger Donjon workspace is actually a separate area from the rest of the office. As we are working with cutting-edge equipment and sensitive information, it is a restricted area protected by an alarm and has a strict access control to our security researchers only. Our team consists of world-renowned security researchers with wide field of expertises to cover all attack surfaces.
What kind of equipment do you use at the attack lab?
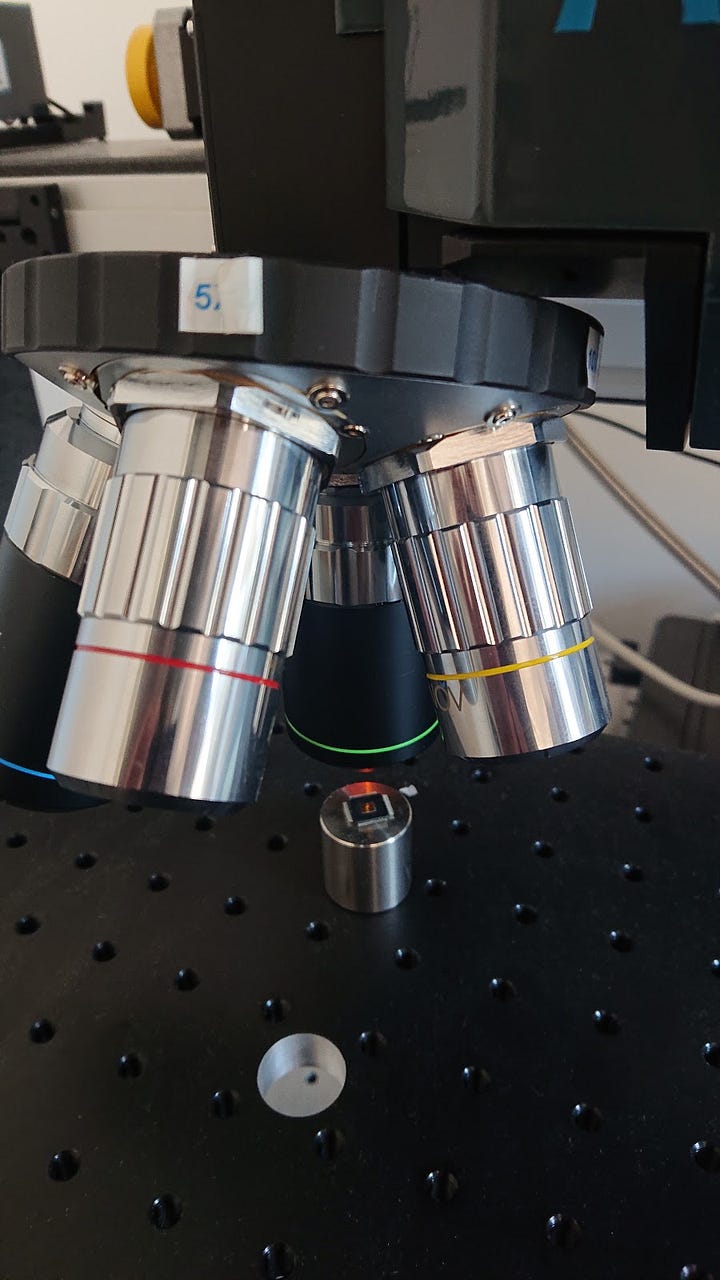
Our security laboratory is highly advanced: we collaborate with major security actors such as Gemalto and ANSSI. We use dedicated tools for software attacks (examples: static analysis, binary reversing and code auditing). We also develop dedicated tools for our needs and share them with the security community. We equally have state-of-the-art equipment for highly sophisticated attacks, such as a sample preparation machine, a laser test bench and a side channel attack bench.

Sample Preparation Machine Laser Test Bench
Side Channel Attack Bench
We put a lot of resources into our research facility because we believe that security is key. To get the best results, the best equipment and researchers are needed. At Ledger, we spare no expense to create the attack lab and raise the bar for keeping the edge against attackers.
To our knowledge, we are the only actor in the cryptocurrency industry to have an internal attack lab, which truly sets us apart from a security point of view.
For our final article, we will discuss certification with Charles and what this means for Ledger.
About Charles Guillemet:
Charles joined Ledger in 2017 as Chief Security Officer after working for 10 years of in the Cryptography & Hardware Security sector. Charles holds a Master of Science in Cryptography & Security at the Engineering School ENSIMAG, with a Major in Cryptography and Security, where he is now a Lecturer.