Product | 11/17/2015
Rethinking digital trust in a post Snowden era

Private companies have been given the keys to our kingdoms, digesting and analyzing petabytes of our personal data. It is not only an obvious breach of our privacy, but also an open door to identity theft, hacks and online extorsions.
The fake president scam is a textbook example of how a company can be stripped of millions of dollars by exploiting basic loopholes in the chain of trust of a given business process. And closer to us mere mortals, the Ashley Madison hack is a demonstration of how data and identity centralization can go very wrong, very fast.
A shift to new privacy and security paradigms
For the last few years, we have seen a gradual change of paradigm in the security, financial and privacy fields. These changes have all one essential thing in common: decentralization.
In a decentralized architecture, there is no single authority that takes decisions on behalf of all the parties nor keeps any kind of information within a walled garden. Instead, each party makes their own local decisions towards their own individual goals.
Let’s explore three major areas being completely disrupted by the decentralization approach.
Digital identitie
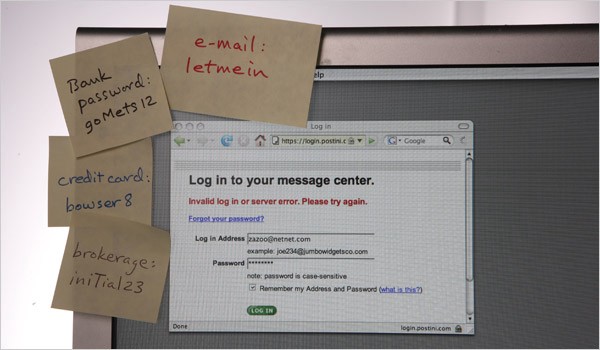
We have dozens of them, and they reign on our digital life. Most of the time, they are an email and a password, and more often that it should be, they share the exact same password. Digital identities are the gateways to all our online services, but they suffer massive flaws:
- you do not own nor control them: they are centralized in third party databases, ripe for hacking or harvesting;
- they leak privacy: if your ID is your email, then most probably your real name is directly attached to it;
- the security is generally weak: servers get hacked, passwords are shared, keylogging or fishing are legion;
In the quest to more security, password managers generate strong passwords and memorize them for you in a digital local safe, protected by a (hopefully last) password. It is good for compartimentalization of the risk, but if a keylogger or malware intercepts your password, this doesn’t help.
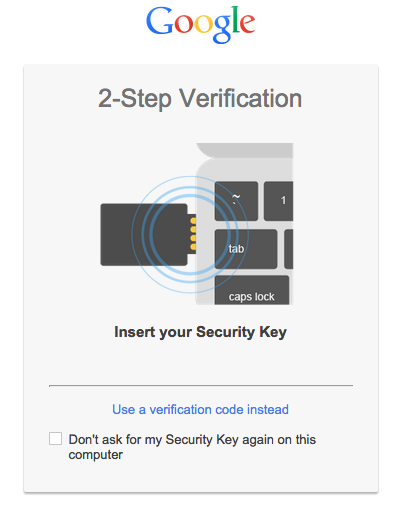
Second factor authentication (or 2FA) is a first step towards decentralization in the sense that it adds a security layer where the user must provide some information (i.e. a time limited code) that only she may know. This code can be sent via SMS, given by a smartphone app or a dedicated USB dongle.
However, the real disruption comes in the form of “passwordless login”.
Getting rid of emails/logins and passwords not only strongly mitigates phishing and hacks, but also prevents privacy leaks. In this configuration, the online service only knows you as a string of seemingly random characters, potentially a “public key”.

The FIDO alliance (Fast IDentity Online) has been given the mission of changing the nature of online authentication by developing a standard and operating industry programs to help ensure worldwide adoption.
Big names of the IT industry are committed at the board member level in FIDO suc as Google, Intel, Samsung, Microsoft, Qualcomm, Paypal, VISA, and Mastercard. They are making sure that global adoption is coming.
Based on asymmetric cryptography, the passwordless experience relies on the signature of a login challenge issued by an online service. The signature is added locally by the user, cannot be replayed, and never leaks any exploitable information. In case of a hack of the online service, identities are not at risk: as they are in full custody (and property) of the user, they cannot be stolen.
Bitcoin
Bitcoin is a decentralized currency and a peer-to-peer payment network. It is the most famous example of a decentralized system, and contains the roots for the most potent disruption of many incumbent financial and trust industries.

At its simplest expression, Bitcoin is digital cash, as in hard cash that you really own. Volatility and other complex issues aside, Bitcoin is a valid answer to the governments push towards a cashless society.
If bank notes and coins disappear, only cryptocurrencies will give users the power to transact on their own terms, and even own their money. When adding the layer of smart contracts made possible by the blockchain technology, Bitcoin can take a seat at the global financial table, and may bring the biggest push towards decentralization.
Electronic signature
Since 1991 and the avent of PGP, electronic communications have all the necessary tools to ensure privacy and authentication of writers. But it is only recently, with the efforts of companies like Keybase, that asymmetric cryptography has been given a simple and accessible UX.
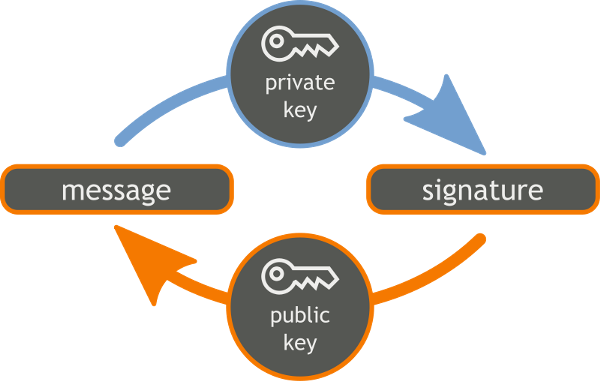
Electronic signature of a document is a major win for modern businesses, removing the paper storage headache and accelerating contract validation.
Not only is a cryptographic signature impossible to fake, it is also very easily verifiable. Using these tools, one can establish a fully trusted communication channel, or implement business practices based on document signatures. With the publication of such contracts on the blockchain for immutable public verification, a totally disruptive technological layer is created.
The rise of new devices of trust
All these examples have something critical in common: they are all based on asymmetric cryptography, which requires that users manage and safeguard their private keys securely.

In a decentralized model, it is up to the end user to ensure this security. Traditional computing platforms such as PCs, MACs and smartphones cannot be trusted with such tasks: as they have not been designed with security in mind, keeping critical data on their disks or memory storages will eventually result in a breach. Malwares and viruses only need to scan files to find private keys and exfiltrate them to an attacker.
In the security industry, the smartcard (or Secure Element) has always been the golden standard. However, it is not adapted to the requirements of the internet. When you insert your credit card in a payment terminal or an ATM, you are using trusted hardware, and when you are prompted to confirm a payment of $100, you know for sure that the machine won’t in fact bill you $10,000.
On your laptop, you cannot trust your hardware at all. Even if your private keys were stored on a smartcard connected to your computer, how do you make sure that your display is showing you the document or the transaction that you are indeed going to sign? You may think that you are signing a transaction to Bob, where you are in fact sending all your funds to Alice.
Bitcoin users know that all too well, and this is why any serious holder manages his funds using a “hardware wallet” which is not only built around a secure element, but has either a trusted display or an integrated second factor verification mechanism.
More generally, the decentralization generates the need for new devices of trust, managing private keys within a secure environment, and featuring trusted displays that allow the user to verify and validate every critical operation.
The Ledger Blue
After several months of R&D, and capitalizing on the experience of its previous Bitcoin hardware wallets products, Ledger is proud to unveil the Ledger Blue, the first new generation personal privacy device.
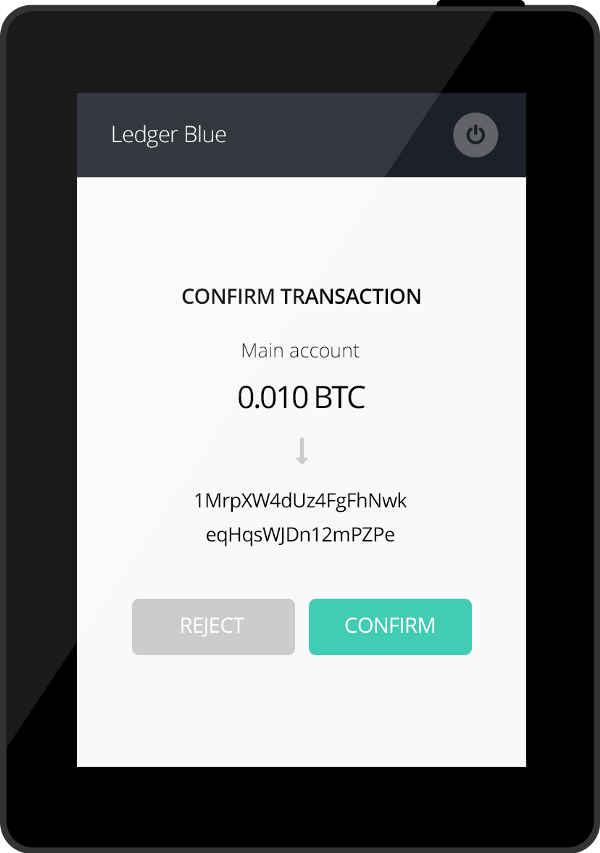
The Ledger Blue is a personal lightweight mobile device with a touchscreen, embedded USB communications and architectured around a ST31 secure microprocessor. By enforcing the user presence and validation on a trusted interface, the Blue brings a strong mitigation to phishing and malware attacks.
Being FIDO compliant, the Blue will be your key to online services such as Google, Dropbox, Github and many more. The Blue also offers all necessary hardware wallets features for Bitcoin, other cryptocurrencies and blockchain tokens. Second factor verification of transactions is done on its secure screen, fully mitigating hacks or malwares.
It also integrates all the necessary features to enable signature and privacy within digital communications, thanks to the strong layer of protection given by the secure element.
Features
- ST31 Secure Element, STM32 MCU
- 320×480 touch screen
- USB 2.0 FS
- 500mA lithium ion rechargeable battery
Developer friendly
The Blue is open source, open architecture and trustless. With a full SDK and an emulator, it will be easy to develop new secure apps leveraging all features of the device.
- High level SDK on the Secure Element. No NDA required.
- Full JTAG developper access on the MCU
- Compatible APIs with our other products (Ledger TEE, Ledger HSM, Ledger Nano)
More information about the Ledger Blue
In January, we will make available 100 developer units with SDK for sale to early enthousiasts. If you want to build secure apps or experiment with the Blue, contact-us now to reserve your unit!
