Product | 12/03/2018
A Closer Look Into Ledger Security: the Secure Element
The coming two weeks, we would like to give you a closer look into what makes Ledger hardware wallets as groundbreaking as they are. This week we will discuss what sets our devices’ security apart. Next week, we will give you a tour in how we are keeping our edge.
For today’s article, let us dig deeper into a critical component of our technology: the Secure Element.

Ledger hardware wallets make use of a specialized secure chip called a Secure Element. These chips provide the highest level of security for a chip, and are much stronger than traditional chips. Secure Elements are used for high-end security solutions such as credit cards and passports. The top-left black square seen inside this Ledger Nano S is what a Secure Element looks like.
What is a Secure Element?
A Secure Element is a secure chip that provides an extra layer of security compared to standard ones. It embeds intrinsic countermeasures against many known attacks. This kind of chip is tamper-resistant and protects your device to a range of different attacks. The smartcard was invented in 1974 by the Frenchman Roland Moreno. The goal of his invention was to manage and secure the access to private data. This could be seen as the start of the Secure Element.
These Secure Elements are nowadays used for many different applications. In all cases, this concerns highly confidential information that needs to be stored securely. Some examples of smart card applications are credit cards, passports and SIM cards. In all of these cases, there is highly sensitive information, such as biometric information, banking and transaction information. Without a secure chip, this could be easily hacked and one could easily take all your money or impersonate you. Inside Ledger’s hardware wallets, we use the Secure Element to generate and store the private keys for your crypto assets. Thanks to the Secure Element, these will not leave your device.

Smart cards are often used in credit cards, but equally in other cards that store sensitive information such as passports and SIM cards.
What kind of protection does a Secure Element provide?
There are several types of attacks which a Secure Element provides protection against. Traditional chips do not contain the same level of security and would not be able to withstand these attacks. We will discuss three type of attacks that a Secure Element mitigates here:
Side-Channel Attack: a “Shazam” for power consumption
When an electronic device processes an input, it produces physical leakages (such as power consumption, or electromagnetic emanation). These physical leakages depend on the data manipulated by the circuit, and are called the side-channels. The listener would use a probe and scope to receive all readings – both input and what’s stored on the chip – in one single curve.
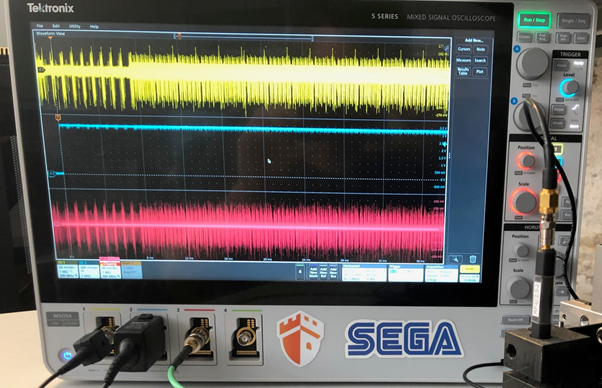
Curves showing power consumption (top) and electromagnetic radiation of a chip during a critical operation that uses the cryptographic key – measuring tools involve probes and digital scope.
The critical operations for your device use cryptographic keys. An attacker can take advantage of the dependency of the power consumption. They would need physical access to your device to do so.
One of these attacks can be compared to the famous music-recognition app Shazam. When there is a song on the radio, Shazam can listen to it and tell you what is currently playing. To do so, Shazam tries to find a match in the extensive library of original songs they’ve built.
With the right tools, you can equally listen to the power consumption. Suppose an attacker has physical access to your device. They could then measure the power consumption of your device. Just like Shazam with sound, a side-channel attack procedure would be able to try and match the power consumption pattern with an entry in the database that corresponds with your cryptographic key.
The listening done through a side-channel attack will take place directly on the chip or somewhere near it to have a good signal quality.. From here, the listener will attempt to match certain elements and make its own “Shazam database” full of tracks, which will eventually allow the listener to crack the PIN code.
This is, however, only one specific form of a side channel attack. There are several others. One might try to read bytes out of the result of listening to the power consumption. Another type would be to check the time it takes to process a specific operation. For example, a correct PIN number being entered might take a tiny bit longer to process, which will be visible in the power consumption.
A Secure Element is specifically designed with complex countermeasures inside the chip. These help to hide the electromagnetic radiation and power usage, protecting it against those who want to listen to its emissions, helping to resist side-channel attacks.
Fault Attacks: applying changes to the circuit while running
A fault attack is the act of perturbing a circuit while it is running. This causes an error within a device or machine, which can lead to either learning more about its functions or even force a different, faulty behavior. Such behavior can include skipping steps of a process or providing a wrong output. All of this is the goal of a fault attack.
Fault attacks can be done by, for instance, changing its voltage with a clock or voltage glitch or more sophisticated disruptions with electromagnetic fields or lasers.
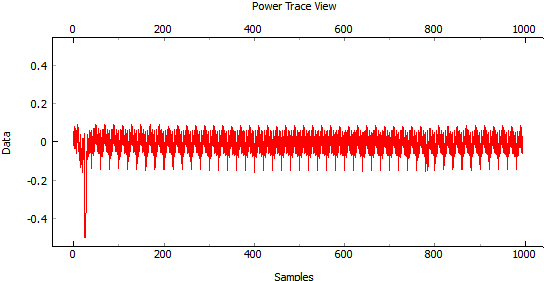
A voltage glitch: as can be seen, there is a large spike to the down-side which is used to try and force faulty behavior. These attacks are time-sensitive, thus only last for a very short time.
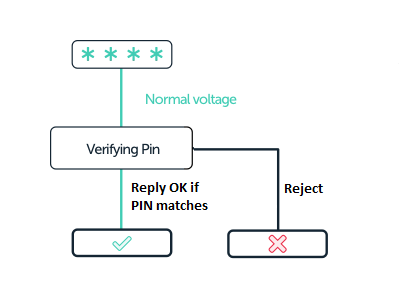
For our example, the figure above shows how a PIN code verification takes place. You enter your PIN, the chip verifies if your PIN entry is correct and then gives an appropriate result.
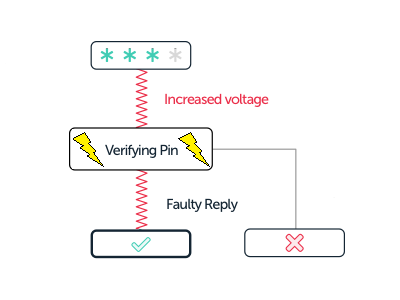
If you change the voltage of the input, the chip might start showing unexpected behavior. The voltage would need to be increased for a very short period of time and at a very specific timing, namely when the verification of the PIN is taking place. This can cause it to suddenly skip the PIN code verification.
A Secure Element has an implementation of countermeasures to prevent these types attacks from succeeding. These allow for an efficient fault detection and appropriate security reactions.
Software Attacks: learning what makes a device tick
Software attacks aim to expose, alter, disable, destroy or steal information. Software attacks can be divided into several types of attacks which all try to find unexpected behaviors obtained by targeting its software. These unexpected behaviors in software are caused by inputs that would normally not be given and can actually show vulnerabilities or give out sensitive information.
We’ll take the example of Heartbleed. Heartbleed is a famous security bug on one of the most popular cryptographic libraries (OpenSSL) which is humoristically described below.
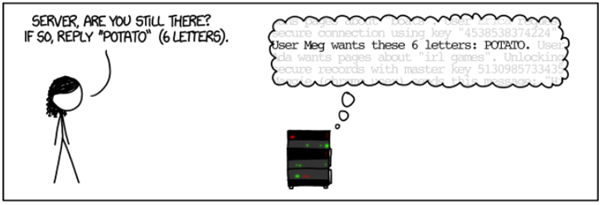
Meg asks the server to reply the word “Potato”, which is 6 letters long. Meg tells the server that she needs a 6 letter response.
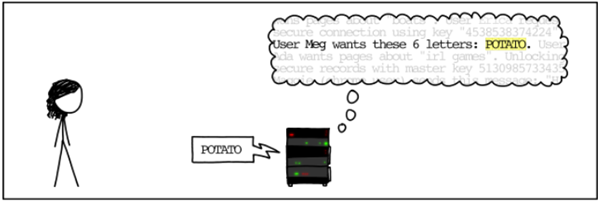
The server correctly responds to Meg with the word “Potato” as asked with the requested 6 letter response.
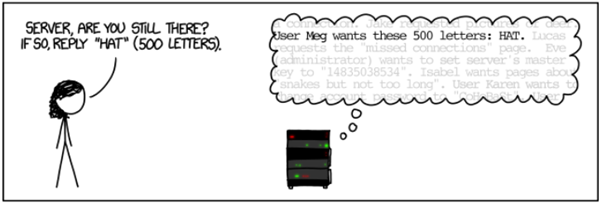
Meg decides to try and see how the server will respond by giving a wrong input: she asks for the word “Hat”, but incorrectly claims that it is a 500-letter word. Playing around with an input is a good way to discover software vulnerabilities.
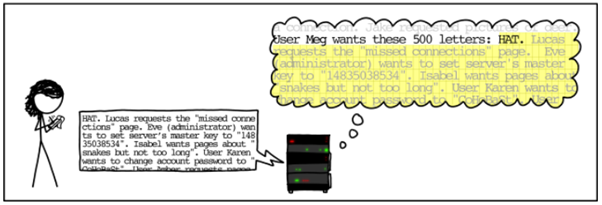
The software of the server does not expect incorrect requests. It recognised the word “Hat”, and consequently responds, however it is tricked into providing much more information.
Here’s where unexpected behavior occurs. The server’s software is coded to oblige to the request for 500 letters and will indeed do so. In this particular example, the server gives Meg sensitive information such as the server’s master key and Karen’s password change.
The Heartbleed bug is but one example of a software attack, but does showcase quite well how they operate. By playing around with inputs, you can learn more about how a device’s software is programmed to react to false inputs. This understanding of the software can then lead to discovering its weaknesses. A Secure Element helps to prevent this type of attack, however. Indeed, it drastically reduces the attack surface by keeping a very simple system that uses very few interfaces.
Conclusion
A Secure Element is a highly advanced chip that mitigates a lot of different types of attacks. This cutting-edge chip, which is used in high-level security solutions, really sets Ledger apart as a top-end security solution for crypto assets. All of our devices use a Secure Element, which greatly enhances their security. Ledger uses them to generate and store the private keys for your crypto assets, keeping them off of any internet-connected device.
In short, Secure Elements are a critical security component of your Ledger device because:
- Secure Elements are the go-to solution for protecting critical data, being the standard for banks to protect credit card information and governments to protect biometric data in passports.
- Secure Elements are designed to withstand highly sophisticated and costly attacks.
- Secure Element chips go through a thorough evaluation done by a third party and need to successfully withstand the attacks described earlier to be able to receive a security certificate.
- Without a Secure Element, critical information (such as PIN codes or even private keys) can be extracted much more easily.
Aside of using a Secure Element, Ledger is the only hardware wallet that combines it with a custom Operating System, called BOLOS. In our next article on Ledger security, we will take a closer look at our proprietary Operating System.






























