Product | 02/20/2019
Lascar: Donjon Side Channel Library
Introducing Lascar
Recently, Ledger Donjon (Security Team) published its open source python3 Side Channel Attack library on github: meet Lascar.
Lascar stands for Ledger’s Advanced Side Channel Analysis Repository. Its goal is to gather and provide common tools and techniques used in the field of Side Channel Analysis, within an open, customizable library.
Based on the principle that published Side Channel Attacks, any scientific piece, should be reproducible, we aim at offering an open source platform for publishing your work.
From our experience, every Side Channel team owns and maintains its own tools, and very few people share their code. This may be caused by very few solutions being available.
Lascar is designed to provide almost everything one would need to complete a state-of-the-art Side Channel Analysis.

Main Features
Lascar provides primitives for all the required steps in Side Channel Analysis. It allows the implementaton of end-to-end Side Channel Attacks. The library offers:
A convenient data representation.
Multi-dimensional Tracesand the corresponding meta-data are stored within the same object. This is good practice for side channel implementations, as it prevents mistakes during the side channel processing where the traces and the corresponding plaintext/ciphertext mismatch. All native data types are supported transparently: int8_t, uint8_t, int16_t, uint16_t, int32_t, uint32_t, int64_t, uint64_t, float, double.
Lascar offers an answer to this problem through the Trace class and ContainerClass.
In Lascar, every side-channel experiment is called a Trace, and is represented as a couple (leakage,value)where:
leakageis a table containing your side-channel(s),valueis a table containing the value manipulated during the acquisition of the leakage,- both leakage and value have to be translatable as a numpy array.
As an extension the Container Class can be seen as a collection of Traces.
No matter the source of your side-channel data:
- stored files of your own format (
npy,hdf5,…) - simulated traces,
- raw traces from your side-channel bench,
| from lascar import * | |
| container = NpyContainer('test_leakages','test_values') # load data |
A set of primitives for resynchronization purposes.
When using classical Side Channel Attacks Methodology, synchronization of traces with each other is key. Through this path, a classical and quite efficient countermeasure consists of introducing jitter, shuffling, randomization, in order to desynchronize traces. Lascar includes a set of useful and easy-to-use primitives for resynchronization purposes including:
- Peak detection
- Pattern detection
- Elastic alignment
| from lascar import * | |
| container = NpyContainer('test_leakages','test_values') # load data | |
| class Synchronization: | |
| def __init__(self, lref): | |
| self.ref_peak_offset = ref.argmax() | |
| def __call__(self, leakage): | |
| #We need to find the peak in each leakage,and roll it to match the ref_peak | |
| peak_offset = leakage.argmax() | |
| return np.roll(leakage, self.ref_peak_offset-peak_offset ) | |
| container.leakage_processing = Synchronisation(ref=container[0].leakage) |
Adding to that, Lascar is very versatile, allowing to add easily user-defined primitives. In Side Channel Attacks, when attacking a new set of traces, some tweaks are often necessary to post-process the traces. That’s why versatility is a key feature.
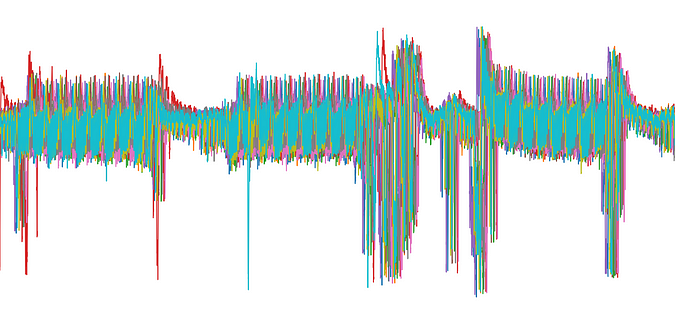
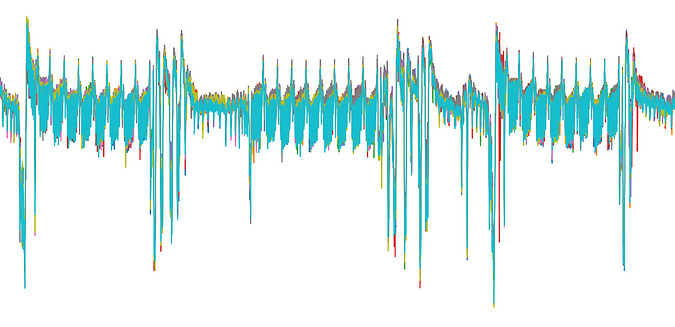
A set of primitives for Side Cannel leakage characterization purposes.
Often, Side Channel Analysis first starts with a characterization. In this situation, the attacker has access to a device on which he knows the key / sensitive value he’s trying to attack. It can be another device, another similar application… In this situation, it’s definitely more efficient to start the analysis with statistical analysis for Side Channel leakage detection. Several of these statistical moments are implemented in Lascar:
- SNR
- NICV
- TTEST
These statistical moments allow the attacker to characterize the dependence between the key / sensitive data and the traces. They are key to performing efficient attacks.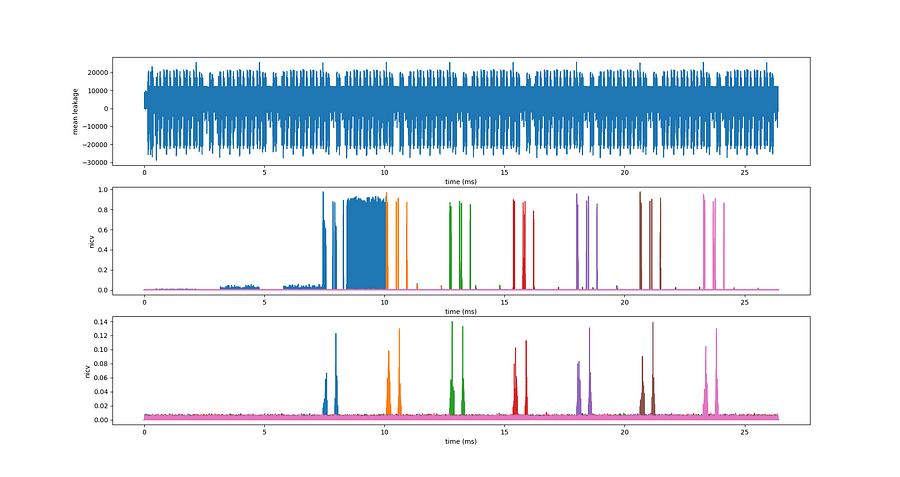
A set of primitives for Side Channel Attacks methodology.
Ultimately, attacks are what we want to do. There are plenty of methodologies to attack a cryptographic (or non-cryptographic) implementation using Side Channel. They range from basic Timing Attacks / SPA, to Supervised High Order Machine Learning Based Attacks. Lascar offers a comprehensive set of attack primitives allowing you to implement your favorite attack.
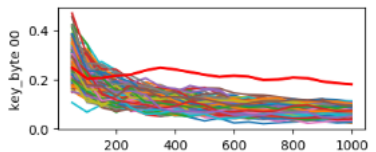
Often, within Side Channel Analysis, the attacker wants to try a lot of different methodologies, combining them in different order to try new ideas. In Lascar’s case, implementing an end-to-end attack is very easy and convenient.
| from lascar import * | |
| from lascar.tools.aes import sbox | |
| filename = "/home/johndoe/ASCAD_data/ASCAD_databases/ATMega8515_raw_traces.h5" | |
| # poi = Points Of Interest. | |
| # We use the SNRs computed before to extract time samples where both mask and masked sensitive variable are used. | |
| snrs = DictOutputMethod.load('SNR.pickle') # we load the snr results computed at 02-snr.py | |
| poi = [] | |
| poi = [snrs['SNR4: masked sbox output in linear parts'][5000].argmax()] | |
| poi += [snrs['SNR5: sbox output mask in linear parts'][5000].argmax()] | |
| # Container creation: we take the same file, but set the leakage_section to the computed poi. | |
| container = Hdf5Container(filename, | |
| leakages_dataset_name="traces", | |
| values_dataset_name="metadata", | |
| leakage_section=poi, | |
| ) | |
| container.number_of_traces = 500 | |
| # Then we make a container that will apply a CenteredProduct to recombine all the points of interest. | |
| container.leakage_processing = CenteredProductProcessing(container) | |
| # Now a classical CPA, targetting the output of the 3rd Sbox: | |
| cpa_engine = CpaEngine("cpa-high-order", | |
| lambda value, guess: hamming(sbox[value['plaintext'][3] ^ guess]), | |
| range(256), | |
| solution=container[0].value['key'][3], | |
| jit=False) | |
| session = Session(container, | |
| engine=cpa_engine, | |
| output_method=ScoreProgressionOutputMethod(cpa_engine), | |
| output_steps=10) # the steps at which the results will be computed | |
| session.run(1000) |
The performance was not the first requirement, but it has not been neglected.
For now, on a standard laptop (i7–8550U @1.8GHz), running a CPA targeting AES SBOX on a set of 100.000 traces of 10.000 samples will take around 25 seconds.
If you are a student interested in learning about Side Channel Attacks, a professional researcher, or an expert in Side Channel Analysis working in a security evaluation lab, Lascar is for you ;-).
Have a look on our Github, fork it, clone it, and don’t hesitate to contribute to its development.
By Ledger Donjon — Manuel San Pedro — Victor Servant— Charles Guillemet






























 by
by