Product | 01/15/2019
Ledger Nano X & Bluetooth – Security Model of a Wireless Hardware Wallet

Ledger recently announced the launch of the Ledger Nano X. This new product is built around a new hardware architecture, while taking advantage of our versatile security Operating System BOLOS.
The Ledger Nano X features Bluetooth Low Energy (BLE) connectivity enabling it to be used with Android or iOS devices without the need of a cable. While this feature greatly improves the user experience, it raised some concerns about the security of the wireless connection. We would like to address these.
In short:
- Only public data is transported by Bluetooth; critical data (such as private keys and seed) never leave the device.
- Even if the Bluetooth connection would be hacked, the security of the Ledger Nano X relies on the Secure Element (SE) which will request your consent for any action.
- The Ledger Nano X Bluetooth implementation uses a state-of-the-art Bluetooth protocol. This Bluetooth protocol ensures authentication by using pairing. This is numeric comparison based and confidentiality is ensured using AES-based encryption.
- If ever, you’re not comfortable using your Nano X with a wireless connection, you can disable the Bluetooth and use the USB type-C cable.
Let’s discuss in more detail how it works and why it does not impact the security model of this hardware wallet.
Architecture
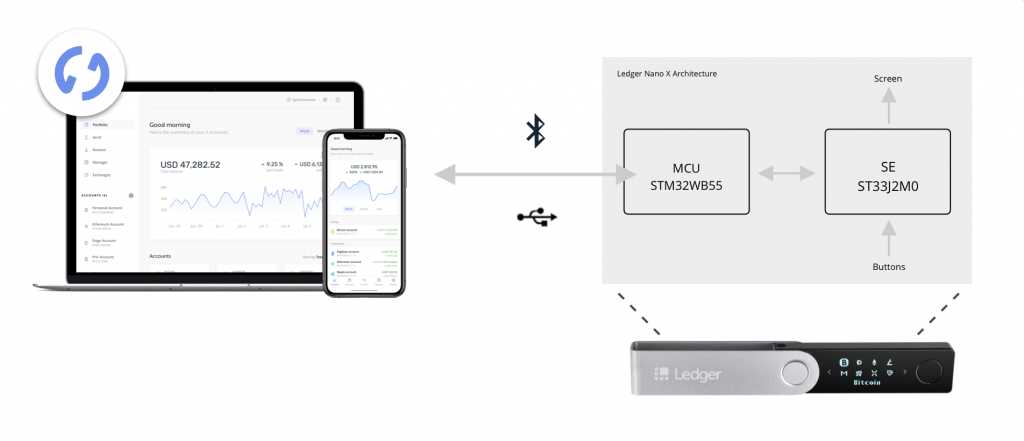
The new architecture is a bit different from the Ledger Nano S one while staying quite similar at the same time.
It features 2 chips:
- A new state-of-the-art Secure Element (ST33J2M0)
- A dual-core MCUs with wireless support (STM32WB55)
The STM32 MCU is in charge of the connection between the smartphone/desktop and the Secure Element and simply acts as a proxy.
The Secure Element is in charge of getting user inputs and driving the screen where critical information is displayed. Of course, it is also in charge of the security of the product. It stores the seed and the private keys and implements all cryptographic operations to manage your cryptocurrencies.
Bluetooth Low Energy
Impact on our security model
Bluetooth connection is only used as a transport layer for public information. The secret keys or seed are never exposed to the BLE stack and never, ever leave the Secure Element.
For instance, when you make a transaction, the transaction is prepared on the smartphone or desktop Ledger Live application and then sent using Bluetooth or USB to the MCU (STM32) which directly relays it to the Secure Element. You are then prompted to verify the amount and the address of the recipient, which are displayed on the screen. If everything is correct you can approve the transaction by pressing both buttons.
If ever your smartphone/computer were compromised, if ever the Bluetooth link was compromised, if ever the STM32 MCU was compromised, the Secure Element ultimately prompts you to verify the transaction information. The screen will show you the true transaction details. No transaction signature is issued without your explicit consent.
Our use of BLE
Nevertheless, the Bluetooth stack may transport your public keys or addresses and this could raise privacy concerns. That is why we implemented a state-of-the-art Bluetooth protocol.
A BLE connection is a 2-phase protocol.
- Key Exchange
- Use of the BLE channel
First of all, both parties (Ledger Nano X and smartphone) generate their own key pairs using a Random Generator.
After this, there is a pairing phase where, after user approval, the Ledger Nano X and the smartphone go through an Elliptic Curve Diffie Hellman key exchange. This phase is critical since it is the phase where the Ledger Nano X trusts the smartphone to which it pairs and vice versa. In order to avoid Man-In-the-Middle attacks (MiTM), which are the common attacks on BLE, the Bluetooth protocol has specific configurations.
We implemented the state-of-the-art security configuration to avoid MiTM attacks: Numeric Comparison. When the common secret is generated, both the Ledger Nano X and smartphone display a numeric code and the user verifies if they are the same. This numeric code is computed using AES-CMAC from public keys of both parties and random nonces. This avoids collision attacks and downgrade attacks, while enforcing the authentication of public keys. If this is the case, both parties consider each other as legitimate and can then communicate, guaranteeing authentication and confidentiality.
Once this key exchange protocol is completed, a secure channel can be established between the smartphone and the Ledger Nano X, featuring an AES-based encryption scheme.
On older versions of Android, the Numeric Comparison may not be featured. In this case, the Secure Element warns the user with a message and a MiTM attack could be implemented. This attack would require an attacker, located nearby, to firstly pair a rogue device with the Ledger Nano X and also with the smartphone. Then he could intercept and forward every packet. This would allow spying on the communication between the Ledger Nano X and the smartphone or even sending commands to the Secure Element. However, the user would still be asked to verify and consent for any transaction.
Security Audit
Our BLE stack is implemented through the ST stack. The Ledger Donjon, our security team, has evaluated the security of this implementation regarding the latest attacks such as Invalid Point attacks.
Good old USB cable
Nonetheless, if you do not feel comfortable using a wireless connection on your Ledger Nano X, you can simply deactivate the Bluetooth connectivity and use the USB type-C connector with your computer to enjoy the remaining features of the Ledger Nano X.

The Ledger Nano X can currently be pre-ordered. Click on the banner underneath for more information.






























